Mandate of Security Operations Centers (SOC) in India

Ensuring Cybersecurity Resilience: The Importance and Mandate of Security Operations Center’s (SOC) and Log Management
With the rapid digitization of businesses and critical sectors, cybersecurity has become a national priority. Recognizing the increasing sophistication of cyber threats, it’s mandatory for organizations to implement Security Operations Centers (SOC) and robust log management frameworks. These measures are essential for regulatory compliance, strengthening cybersecurity resilience, safeguarding sensitive data, and ensuring business continuity.
Why SOC and Log Management Are Essential
A well-established SOC provides real-time monitoring, threat detection, and incident response capabilities, helping organizations proactively address potential cyber risks. Effective log management ensures comprehensive data collection, retention, and analysis—critical for identifying security incidents, maintaining compliance, and improving overall security posture.
Mandatory Requirements for SOC Implementation
- Establishing a Security Operations Center (SOC)
- Required for financial institutions, healthcare providers, critical infrastructure operators, and data-centric businesses.
- Ensures national security and data integrity.
- Real-Time Threat Monitoring and Detection
- CERT-In mandates continuous network monitoring, threat detection, and response.
- Deployment of SIEM systems is strongly recommended for compliance.
- Incident Response and Compliance Reporting
- As per the IT Act, 2000, organizations must establish an incident response strategy.
- Timely reporting of security incidents to CERT-In is mandatory.
- Continuous Security Enhancements
- Regular security audits, process improvements, and technology upgrades are required.
- CERT-In mandates periodic reviews of security infrastructure.
Mandatory Log Management Requirements
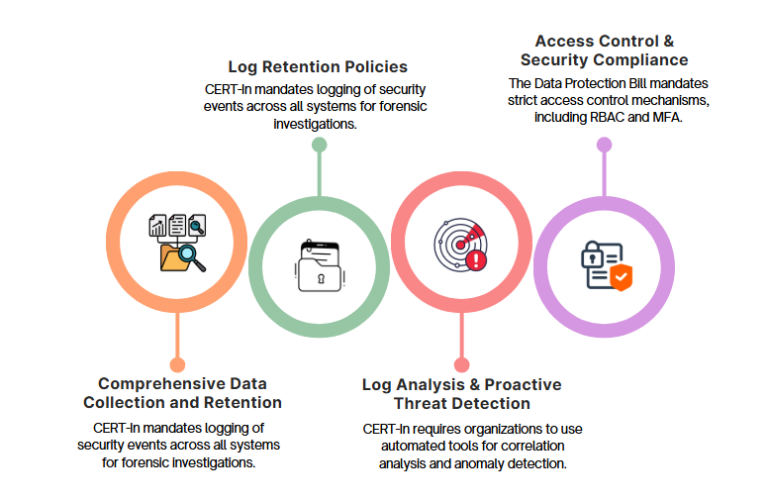
Regulatory Framework and Compliance Enforcement
- Information Technology (IT) Act, 2000 [Ref: meity.gov.in]: Enforces security best practices and legal compliance.
- Reserve Bank of India (RBI) Directives [Ref: rbi.org.in]: Requires SOC implementation in financial institutions.
- Digital Personal Data Protection Act, 2023 [Ref: meity.gov.in]: Enforces strict security measures, including logging and monitoring.
- CERT-In Guidelines [Ref: cert-in.org.in]: Mandates real-time monitoring and log retention.
Conclusion
Implementing a Security Operations Center (SOC) and an effective log management system is crucial for securing digital assets and maintaining regulatory compliance. By adopting these measures, organizations fulfill their legal obligations, strengthen cybersecurity, and ensure resilience against cyber threats, fostering a secure and digitally empowered India.
Ensure uninterrupted protection with 24/7 real-time threat monitoring. Detect and respond to suspicious activity instantly, safeguarding your business from potential breaches.
Contact us today for a FREE Consultation!



